The CompTIA Security + SY0-501 exam is the most popular exam in the CompTIA certification exam. If you want to pass the quick exam, then getting the SY0-501 pdf dumps is the easiest way to get the SY0-501 certification in the shortest time. https://www.pass4itsure.com/sy0-501.html can help people quickly obtain SY0-501 certification. Here are free and up-to-date SY0-501 practice exams.
[free] SY0-501 pdf dumps are here: https://drive.google.com/open?id=1ha5qYtI5h6Ft9bhr3cRN-pn8gxjbRR2W
Where can I get CompTIA SY0-501 dumps questions?
I would recommend the Pass4itsure SY0-501 dumps as the best SY0-501 study guide because it is very helpful for the exam.
Pass4itsure discount code 2020

CompTIASY0-501 practice test questions and answers 1-13
QUESTION 1
Ann, a security administrator, wants to ensure credentials are encrypted in transit when implementing a RADIUS server
for SSO. Which of the following are needed given these requirements? (Select TWO)
A. Public key
B. Shared key
C. Elliptic curve
D. MD5
E. Private key
F. DES
Correct Answer: AE
QUESTION 2
Which of the following differentiates a collision attack from a rainbow table attack?
A. A rainbow table attack performs a hash lookup
B. A rainbow table attack uses the hash as a password
C. In a collision attack, the hash and the input data are equivalent
D. In a collision attack, the same input results in different hashes
Correct Answer: A
QUESTION 3
A forensic investigator has run into difficulty recovering usable files from a SAN drive. Which of the following SAN
features might have caused the problem?
A. Storage multipaths
B. Deduplication
C. iSCSI initiator encryption
D. Data snapshots
Correct Answer: B
QUESTION 4
The SSID broadcast for a wireless router has been disabled but a network administrator notices that unauthorized users
are accessing the wireless network. The administer has determined that attackers are still able to detect the presence of
the wireless network despite the fact the SSID has been disabled.
Which of the following would further obscure the presence of the wireless network?
A. Upgrade the encryption to WPA or WPA2
B. Create a non-zero length SSID for the wireless router
C. Reroute wireless users to a honeypot
D. Disable responses to a broadcast probe request
Correct Answer: D
QUESTION 5
Which of the following is the appropriate network structure used to protect servers and services that must be provided to
external clients without completely eliminating access for internal users?
A. NAC
B. VLAN
C. DMZ
D. Subnet
Correct Answer: C
QUESTION 6
An organization wants to implement a solution that allows for automated logical controls for network defense. An
engineer plans to select an appropriate network security component, which automates response actions based on
security threats to the network. Which of the following would be MOST appropriate based on the engineer\\’s
requirements?
A. NIPS
B. HIDS
C. Web proxy
D. Elastic load balancer
E. NAC
Correct Answer: A
QUESTION 7
Which of the following network vulnerability scan indicators BEST validates a successful, active scan?
A. The scan job is scheduled to run during off-peak hours.
B. The scan output lists SQL injection attack vectors.
C. The scan data identifies the use of privileged-user credentials.
D. The scan results identify the hostname and IP address.
Correct Answer: B
QUESTION 8
A security administrator discovers that an attack has been completed against a node on the corporate network. All
available logs were collected and stored.
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been
compromised and drag and drop the appropriate actions to complete the incident response on the network. The
environment is
a critical production environment; perform the LEAST disruptive actions on the network, while still performing the
appropriate incident responses.
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of the node(s) that have
been compromised and drag and drop the appropriate actions to complete the incident response on the network. Not all
actions may be used, and order is not important. If at anytime you would like to bring back the initial state of the
simulation, please select the Reset button. When you have completed the simulation, please select the Done button to
submit
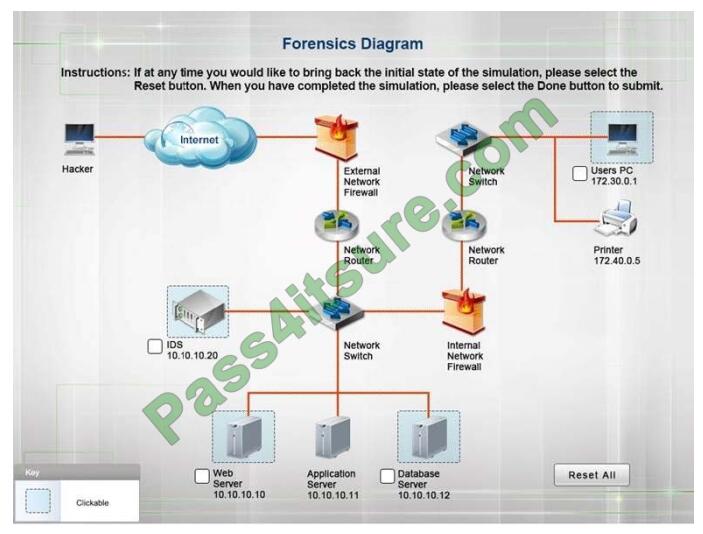
Once the simulation is submitted, please select the Next button to continue.
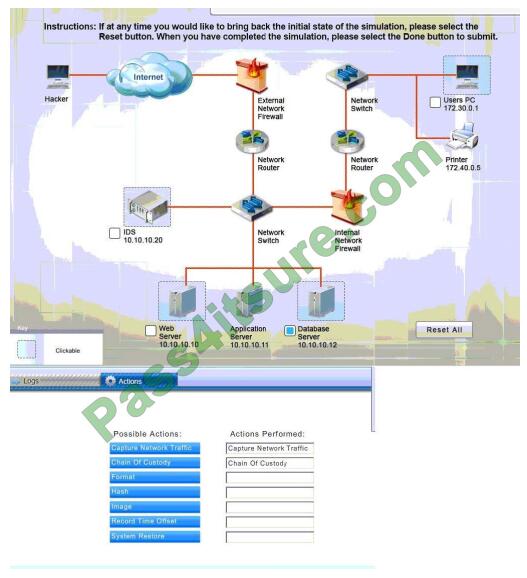
Correct Answer:
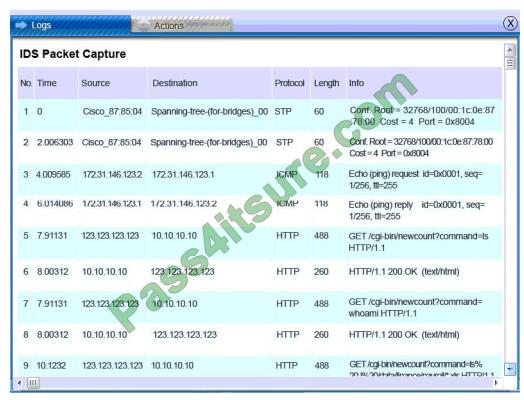
Database server was attacked; actions should be to capture network traffic and Chain of Custody.
(The database server logs shows the Audit Failure and Audit Success attempts)It is only logical that all the logs will be
stored on the database server and the least disruption action on the network to take as a response to the incident would
be
to check the logs (since these are already collected and stored) and maintain a chain of custody of those logs.
IDS Server Log:
Web Server Log: Database Server Log:
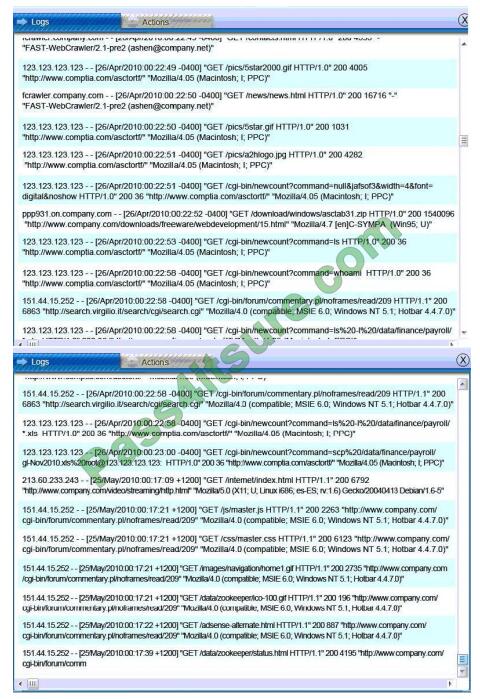
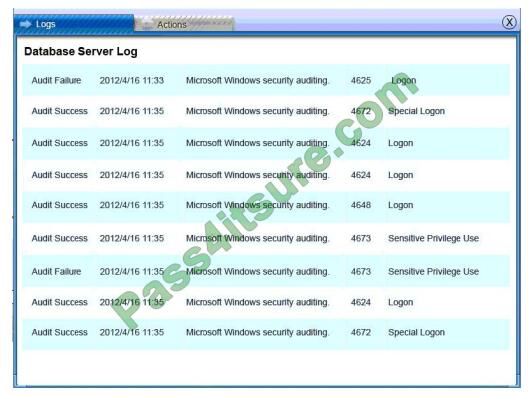
Users PC Log:
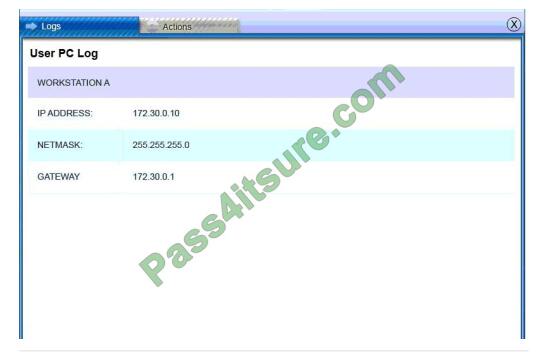
QUESTION 9
Which of the following is an important step to take BEFORE moving any installation packages from a test environment
to production?
A. Roll back changes in the test environment
B. Verify the hashes of files
C. Archive and compress the files
D. Update the secure baseline
Correct Answer: B
QUESTION 10
The Chief Executive Officer (CEO) of a major defense contracting company a traveling overseas for a conference. The
CEO will be taking a laptop.
Which of the following should the security administrator implement to ensure confidentiality of the data if the laptop were
to be stolen or lost during the trip?
A. Remote wipe
B. Full device encryption
C. BIOS password
D. GPS tracking
Correct Answer: B
QUESTION 11
A security administrator is configuring a new network segment, which contains devices that will be accessed by external
users, such as web and FTP server. Which of the following represents the MOST secure way to configure the new
network segment?
A. The segment should be placed on a separate VLAN, and the firewall rules should be configured to allow external
traffic.
B. The segment should be placed in the existing internal VLAN to allow internal traffic only.
C. The segment should be placed on an intranet, and the firewall rules should be configured to allow external traffic.
D. The segment should be placed on an extranet, and the firewall rules should be configured to allow both internal and
external traffic.
Correct Answer: D
QUESTION 12
A user typically works remotely over the holidays using a web-based VPN to access corporate resources. The user
reports getting untrusted host errors and being unable to connect. Which of the following is MOST likely the case?
A. The certificate has expired
B. The browser does not support SSL
C. The user\\’s account is locked out
D. The VPN software has reached the seat license maximum
Correct Answer: A
QUESTION 13
Users are attempting to access a company\\’s website but are transparently redirected to another websites. The users
confirm the URL is correct. Which of the following would BEST prevent this issue in the futue?
A. DNSSEC
B. HTTPS
C. IPSec
D. TLS/SSL
Correct Answer: A
Latest Security+ SY0-501 dumps practice test questions and answers
Get Best SY0-501 Dumps PDF for your Real success in the SY0-501 Exam with Actual SY0-501 Questions Answers.
Best SY0-501 Dumps PDF https://drive.google.com/open?id=1ha5qYtI5h6Ft9bhr3cRN-pn8gxjbRR2W
If you think you are a smart expert and can take the CompTIA SY0-501 exam, you should definitely try it. You can use the latest SY0-501 dumps pdf to start preparing for the SY0-501 exam, https://www.pass4itsure.com/sy0-501.html Q&As: 735.