Certfans is a blog that shares free exam dumps, we update all year round, and we help all friends who need to
open the door to learning. Latest CompTIA A+ 220-902 exam dumps from pass4itsure CompTIA experts,
free online 220-902 exam exercises and 220-902 PDF downloads, If you want to pass the 220-902 exam
for the first time, please select the full and effective 220-902 questions and answers.
https://www.pass4itsure.com/220-902.html provides PDF + VCE mode to help you easily get a certificate
[PDF] Free CompTIA A+ 220-902 dumps download from Google Drive:
https://drive.google.com/open?id=1I4jaW20oyakGy4HS1-ZpIJK_QmwUPEEZ
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
220-902 – CompTIA IT Certifications:https://certification.comptia.org/docs/default-source/exam-objectives/comptia-a-220-902-exam-objectives.pdf
Pass4itsure offers the latest CompTIA A+ 220-902 practice test free of charge (50Q&As)
QUESTION 1
A user regularly calls and states that they have a computer with possibly corrupt system files and wants to know how to repair them. Which of the following utilities would resolve the problem?
A. ASR
B. FIXMBR
C. SFC
D. MSCONFIG
Correct Answer: C
QUESTION 2
Joe, a technician, recently built a new gaming PC for Ann, a customer, with two hard drives configured in RAID 0. Ann calls and states she was playing a game online and the computer shut off. Now the computer will not boot. Which of the
following is a cost effective way to correct the issue?
A. Remove both drives from the RAID array
B. Reformat both drives and reload windows
C. Replace both of the drives and load windows
D. Replace one of the drives and rebuild the array
Correct Answer: B
QUESTION 3
A user is having difficulty installing a program in Windows Vista, as the computer appears to stall prior to the installation. Which of the following is the BEST choice of why this is occurring?
A. Aero Settings are not enabled.
B. Power Settings need to be enabled.
C. BitLocker is scanning for corrupt software.
D. UAC is waiting for user input.
Correct Answer: D
QUESTION 4
A technician is trying to remove a resilient computer virus. The virus keeps coming back after rebooting the system because some program or service has locked some of the virus’ files and is preventing the AV from cleaning the system.
Which of the following is the BEST approach to try and remove the virus while minimizing negative impact to the system?
A. Use REGSRV32 to deregister the virus DLLs.
B. Run the antivirus after rebooting in safe mode.
C. Use the repair disk and follow the prompts.
D. Use the recovery console to disable all windows services.
Correct Answer: B
QUESTION 5
A SOHO has had several issues with various unauthorized devices consuming the network’s bandwidth. There are only four network devices that are authorized to access the Internet as well as the local LAN’s resources. Which of the
following security implementations would MOST likely help disable network access to the unauthorized devices?
A. Using complex passwords
B. Disabling the use of static IP addresses
C. Disabling ports
D. MAC filtering
Correct Answer: D
QUESTION 6
A technician is troubleshooting a reported wireless connectivity problem with a user’s laptop. The 802.11a access point is located in one of the corners of a square office with 100 meter walls, while the user’s office is on the opposite corner.
The user’s laptop is able to wirelessly pair with a printer located in the middle of the office and the user can print in ad hoc mode. Which of the following is the reason the user is unable to connect to the Internet?
A. 802.11a only supports ad hoc mode.
B. The laptop NIC is faulty.
C. RF signal is not received from the WAP.
D. The printer is not connected to the WAP.
Correct Answer: C
QUESTION 7
A technician is installing a new operating system. The company policy requires that the file system used must support file permissions and security. Which of the following should the technician use to BEST meet the company needs?
A. NTFS
B. CDFS
C. FAT32
D. UDF
Correct Answer: A
QUESTION 8
Which of the following are encrypted protocols? (Select TWO).
A. TELNET
B. SSH
C. POP3
D. FTP
E. HTTPS
Correct Answer: BE
QUESTION 9
Which of the following can be used to help recover a lost smartphone?
A. Remote support software
B. Locator application
C. NFC enabled device
D. GPS navigation software
Correct Answer: B
QUESTION 10
An employee recently departed under bad terms, and the client is concerned for their SOHO network security. Which of the following should the technician do FIRST?
A. Physically secure the access point
B. Change default password
C. Lower the transmission power
D. Assign static IP addresses
Correct Answer: B
QUESTION 11
A technician is tasked with resolving a display issue with a laptop. The technician has determined that the laptop’s display needs to be replaced. Which of the following is the NEXT step the technician should perform?
A. Identify the problem that caused the display to fail.
B. Establish a theory of the probable cause.
C. Verify full system functionality and implement preventive measures.
D. Establish an action plan to resolve the problem.
Correct Answer: D
QUESTION 12
An administrator, Ann, wants to be able to access a customer’s router interface from a remote location. Ann always has to have the customer print out the current router settings before she can remotely manage the router. Which of the
following should Ann do to eliminate this extra step before connecting to the router remotely?
A. Change the default user name and password
B. Request a static IP from the ISP
C. Enable the remote management port
D. Enable port forwarding on the router
Correct Answer: B
QUESTION 13
A SOHO location is being remodeled and the users are concerned about unauthorized traffic on their network during the remodel. The WLAN needs to be able to allow various types of devices to securely connect 24 hours a day while
requiring the least amount of overhead to manage. Which of the following security implementations would MOST likely be implemented?
A. Setting encryption
B. Resetting all user-names and passwords
C. Assign static IP addresses
D. Enable MAC filtering
Correct Answer: A
QUESTION 14
A user recently installed an application. Upon the next reboot, the system is displaying various errors relating to the system files and certain actions e.g. right-clicking no longer works. The user does not have time to reimage the computer, nor
do they wish to remove and reinstall the application. Which of the following should the technician do FIRST?
A. Open up the command prompt and type SFC /SCANNOW
B. Open Task Manager and stop all running SERVICES processes
C. Open up MSCONFIG and remove the application from the start-up tab
D. Open a command prompt and type REGSVR32 SYSMAIN.DLL ?U
Correct Answer: A
QUESTION 15
A user on a domain PC needs to leave their desk immediately, but does not want to compromise displayed content. Which of the following should be done?
A. Screensaver password
B. Restart PC
C. Lock screen
D. Reset user password
Correct Answer: C
QUESTION 16
A user calls the corporate helpdesk stating that their battery is not charging. The operating system shows that there is a problem with the battery. Which of the following should the technician do FIRST to determine what the issue is without
erasing the user’s unsaved data?
A. Using a known-good computer of the same type, switch batteries between the two laptops.
B. Remove the A/C adapter while the system is running and observe if the screen dims.
C. Completely shut down the laptop, remove the A/C power source and restart the laptop.
D. Using a known-good computer of the same type, switch A/C adapters between the two laptops.
Correct Answer: A
QUESTION 17
Joe, a client, wants to allow only specific portable devices to connect to his wireless network. Which of the following methods would BEST accomplish this?
A. Disabling SSID broadcast
B. MAC filtering
C. Lower radio power levels
D. Directional antennas
Correct Answer: B
QUESTION 18
A server is configured to boot with a “mirrored” RAID configuration. Which of the following BEST describes this configuration?
A. RAID 0
B. RAID 1
C. RAID 3
D. RAID 5
Correct Answer: B
QUESTION 19
Which of the following methods of securing mobile devices will prevent data loss due to corruption?
A. Enforce pass code locks
B. Install location monitoring application
C. Perform remote wipe after failed login
D. Perform remote application back-up
Correct Answer: D
QUESTION 20
A user’s computer consistently shuts down several minutes after booting. When the technician reboots the computer, a message stating “CPU fan failure” appears. Which of the following is the MOST likely reason the computer shuts down?
A. Overheating
B. Power supply failure
C. Faulty CPU
D. High humidity
Correct Answer: A
QUESTION 21
Which of the following resources is MOST important for a network server running a virtual machine and guest operating systems?
A. Redundant power supplies
B. Memory speed
C. RAID type used
D. Multi-core CPU
Correct Answer: D
QUESTION 22
A user calls the helpdesk to report that print jobs coming from a laser printer in the office are losing most of their toner due to being touched by hand smudge. The printer was recently serviced with a new fuser unit. Which of the following
problems is MOST likely affecting the printer?
A. The fuser is not heating up to proper temperature levels necessary.
B. The pickup rollers are likely dirty and leaving paper dust on all printed pages.
C. The printer’s firmware was not updated with the installation of the new fuser.
D. The fuser was installed backwards and is not evenly heating printed pages.
Correct Answer: A
QUESTION 23
A user states that they see a warning on their screen about an IP conflict. Which of the following is MOST likely the cause?
A. A static IP address is assigned to the workstation
B. A bad router
C. A bad switch
D. The computer is getting an APIPA address
Correct Answer: A
QUESTION 24
An administrator has advised against providing any information over the phone as a way to prevent against which of the following threats?
A. Session hijacking
B. Social engineering
C. Man-in-the-middle
D. Shoulder surfing
Correct Answer: B
QUESTION 25
Following an authorized person through a door or other security check point without showing proper identification or defeating a security mechanism is known as which of the following?
A. Hacking
B. Emulating
C. Partitioning
D. Tailgating
Correct Answer: D
QUESTION 26
Which of the following is the MAIN difference between a rootkit and a virus?
A. Rootkits encrypt the operating system while viruses encrypt documents
B. Rootkits execute as super user while viruses execute as regular users
C. Rootkits modify the BIOS while viruses cannot access the BIOS
D. Rootkits infiltrate the kernel while viruses infiltrate files
Correct Answer: D
QUESTION 27
Which of the following provides Bob, a technician, with the GREATEST security?
A. Disabling SSID
B. WEP
C. Static IP
D. WPA
Correct Answer: D
QUESTION 28
A laptop’s number lock and scroll lock lights are blinking in a certain sequence and is not booting. Which of the following would a technician do FIRST in this situation?
A. Install a replacement memory module.
B. Consult the manufacturer website for diagnostic codes.
C. Attempt to boot into safe mode.
D. Install a replacement hard drive.
Correct Answer: B
QUESTION 29
Which of the following is the correct socket type for a Pentium 4 processor?
A. 478
B. 939
C. 1366
D. AM2+
Correct Answer: A
QUESTION 30
A technician is using a test tool that is displaying the current voltage output of a power supply on the tool. Which of the following tools is the technician using?
A. Loopback plug
B. Cable tester
C. POST card
D. Multimeter
Correct Answer: D
QUESTION 31
An administrative assistant receives a phone call from the IT department asking for personal information to update their records. One of the questions asked is the password to the company’s administrative portal. Which of the following is
occurring?
A. Shoulder surfing
B. Configuration management
C. Helpdesk troubleshooting methodology
D. Social engineering
Correct Answer: D
QUESTION 32
A new LAN drop has been activated but users report that they are unable to connect to the Internet and are receiving an IP address of 169.254.255.55 from that Windows workstation. Which of the following symptoms has occurred? (Select
TWO).
A. DHCP server unavailable
B. IP address assigned by NAT
C. Limited connectivity
D. APIPA address assigned
E. IP conflict detected
F. Statically assigned IP address
Correct Answer: AD
QUESTION 33
An unattended install is MOST likely used for which of the following scenarios?
A. When a technician has a workstation with a defective optical media drive.
B. When a technician is going to be on vacation, but wants to configure a system at a certain time while gone.
C. When a technician wishes to update a user’s system without the user’s knowledge.
D. When a technician has numerous network connected workstations to image.
Correct Answer: D
QUESTION 34
A technician has been dispatched to a SOHO to troubleshoot an issue with a USB printer shared on the network. All networked devices obtain their IP address automatically from the router. Additionally, all computers were printing fine the
previous day, when the printer was first installed. Which of the following should the technician implement to fix the printing issue?
A. A DHCP reservation should be made for the host computer.
B. The printer should be connected to a USB hub.
C. An updated printer driver should be installed on all office computers.
D. The printer should be configured with a static IP address.
Correct Answer: A
QUESTION 35
A technician has developed training material to ensure employees physically secure company laptops from being stolen. Which of the following is a preventative directive that MUST be included in the training material?
A. RFID tags must be attached to all laptops and receivers to all doors to alert when a laptop leaves the designated area.
B. Biometrics devices must be installed on all laptops.
C. All computers must be equipped with privacy filters.
D. Employees must remember to lock their office doors when leaving even for a short period of time.
Correct Answer: D
QUESTION 36
A user reports their laptop is shutting down each time they are idle for a short period of time. Which of the following options would the technician use to remedy the issue?
A. Disk Management
B. Power Options
C. Display
D. System Performance
Correct Answer: B
QUESTION 37
A user requires a remote connection that will allow them to securely access the corporate network of their employer. Which of the following types of connections would be created? (Select TWO).
A. AES
B. RDC
C. TKIP
D. VPN
E. WEP
Correct Answer: BD
QUESTION 38
Joe, a technician, is asked by another technician at his company to identify the host name of a device using a specific IP address. Which of the following commands would be used to obtain this information?
A. NSLOOKUP
B. IPCONFIG
C. PING
D. NETSTAT
Correct Answer: A
QUESTION 39
Which of the following commands is used to duplicate a directory from one location to another?
A. MOVE
B. COPY
C. XCOPY
D. EDIT
Correct Answer: C
QUESTION 40
Which of the following accounts should be disabled after successful installation of Windows XP?
A. Remote Desktop User
B. Administrator
C. Guest
D. Power User
Correct Answer: C
QUESTION 41
Which of the following utilities should be used before installing new hardware in a computer?
A. System File Checker
B. Windows Updates
C. Security Center
D. System Restore
Correct Answer: D
QUESTION 42
A user wants to view and change the file name extensions. Which of the following options in the control panel should be used to accomplish this?
A. Folder Options
B. System
C. Security Center
D. User Accounts
Correct Answer: A
QUESTION 43
Which of the following describes the function of a firewall?
A. Hardware or software designed to analyze data packets to determine the origin or destination of the packet
B. Hardware or software designed to block packets based on traffic behavior over time
C. Hardware or software designed to compare data packets to known signatures
D. Hardware or software designed to block certain packets from entering or leaving a network
Correct Answer: D
QUESTION 44
Which of the following BEST describes geotracking?
A. An enabled cookie that sends user location data to vendors
B. Location software to locate a user’s missing cellular device
C. SMS information that is sent to people in their contacts
D. Location data embedded into pictures that have been taken
Correct Answer: D
QUESTION 45
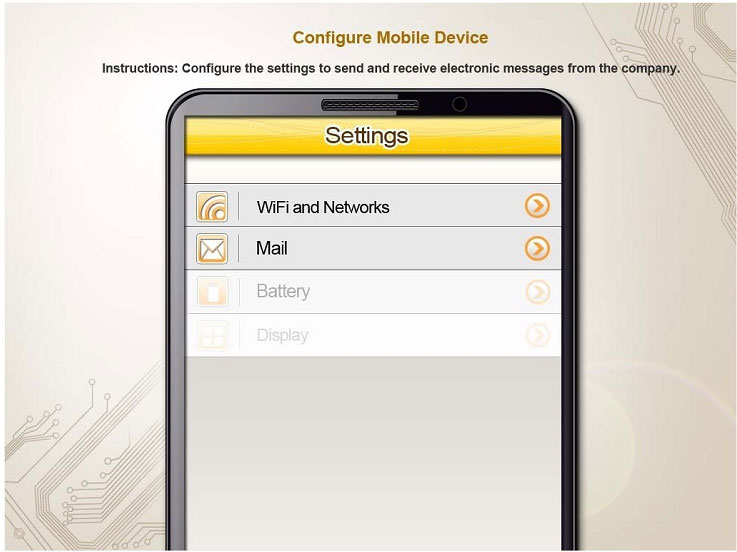
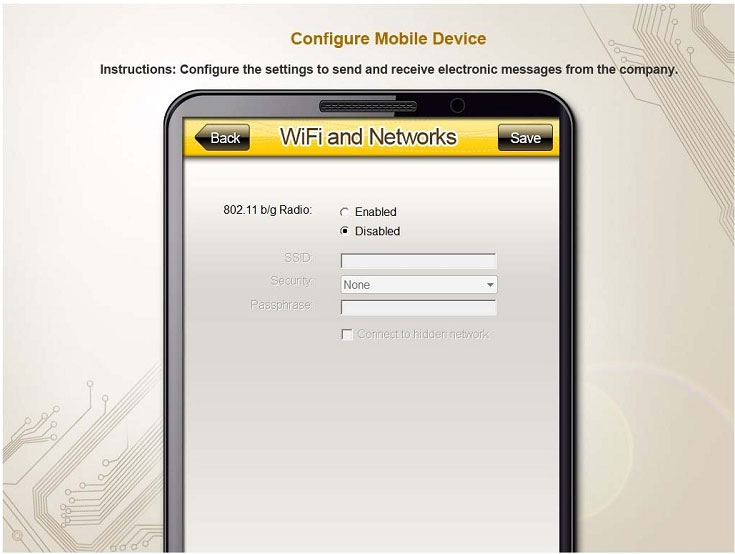
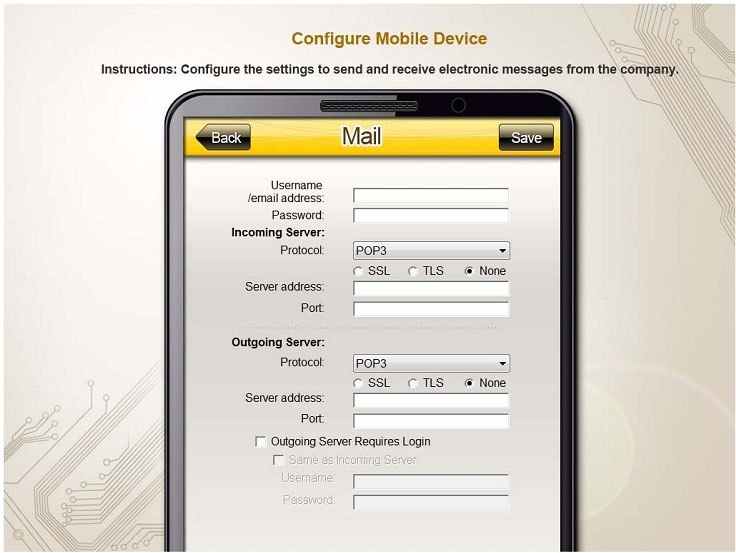
You need to configure your mobile device to send and receive electronic messages from your company. Your mobile device must be able to truly synchronize the message state with your desktop, so that when a message is read on your
desktop, it is marked as read on your mobile device. These are the proper parameters:
Email address: [email protected]
Password: P@$$w0rd
Pop.techies.com Port: 110 Security: None
IMAP.techies.com Port: 993 Security: SSL
smtp.techies.com Port: 465 Security: TLS
Company SSID: Techies
Security: WPA2
Passphrase: P@$$w0rd
SSID is not broadcasted
Instructions: You are not authorized to use the Company’s WLAN. The outgoing server does not require login credentials. When you have completed the simulation, please select the done button to submit your answer.
Correct Answer: Review the explanation for all details.
QUESTION 46
A Windows 7 machine appears to have a failure. Every time it is rebooted, the message “BOOTMGR is missing” appears. You have previously inserted a Windows 7 installation DVD into the DVD-ROM. Please repair this failure without
overwriting the customers’ local user profiles.
Instructions:
Launch the simulation to repair the failure
Type Help in command line to show list of available commands
When you have completed the simulation, please select the done button
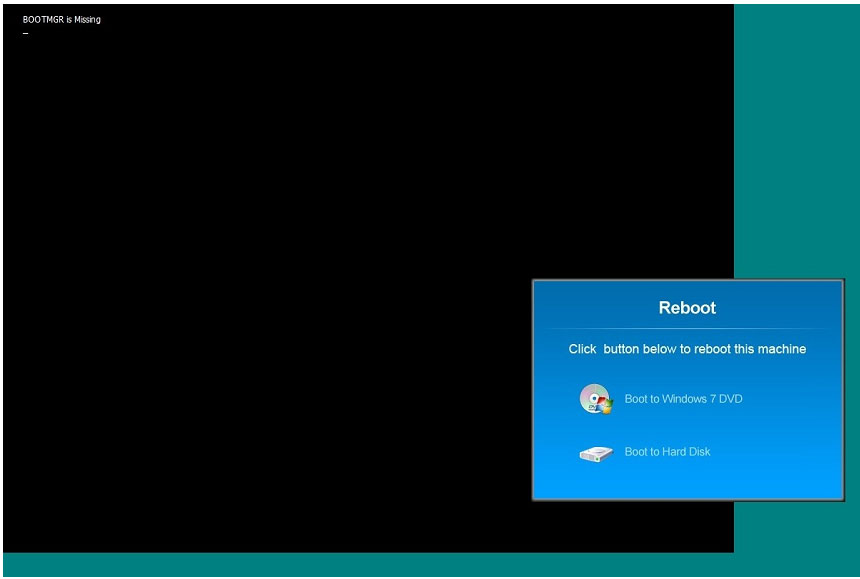
Correct Answer: Review the explanation for all details.
QUESTION 47
A user has installed two new drives in one of the computers in the computer lab and has been unable to format Disk1 from the command prompt. The lab requires that Disk1 be a dynamic disk configured with two partitions. The first partition
must be 256,000 MB in size and mapped to drive F. The second partition must be 512,000 MB in size and mapped to drive G.
The new partitions must be formatted to ensure that users’ files can be secured from other users and that the disk must be configured to account for future redundancy.
Instructions: Conduct the necessary steps within the Disk Manager to accomplish these tasks. When you have completed the simulation, please select the Done button to submit
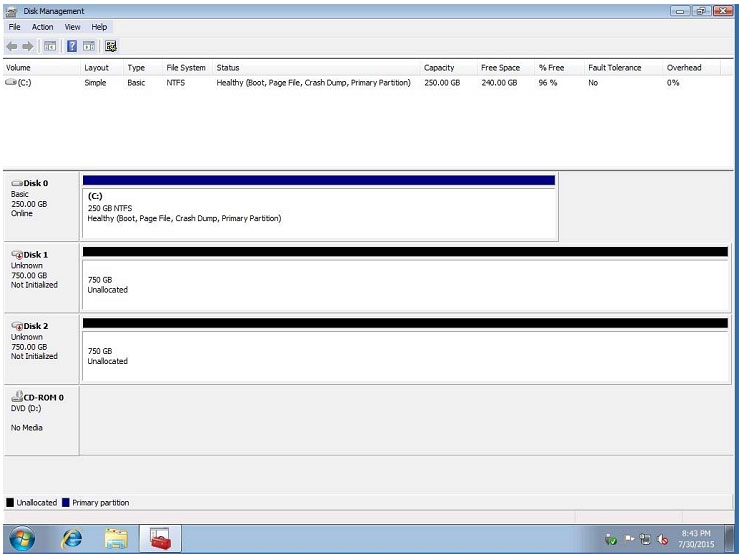
Correct Answer: Review the explanation for all details.
QUESTION 48
You have been tasked with setting up a new executive’s laptop on his home network. After an investigation, you find that his home network is wired and has the following settings:
IP range is 10.10.10.0
Netmask is 255.255.255.0
Default gateway is 10.10.10.1
Additionally, the router’s address is used as the primary DNS server and WINS is not in use.
Please configure the laptop with an IP address of 10.10.10.15, ensuring that the laptop will still work when plugged into the switch at the office, which is configured for DHCP. Do not make any other unnecessary configurations to the laptop.
Instructions: Keyboard shortcuts are not available. When you have completed the simulation, please select the done button to submit your answer.
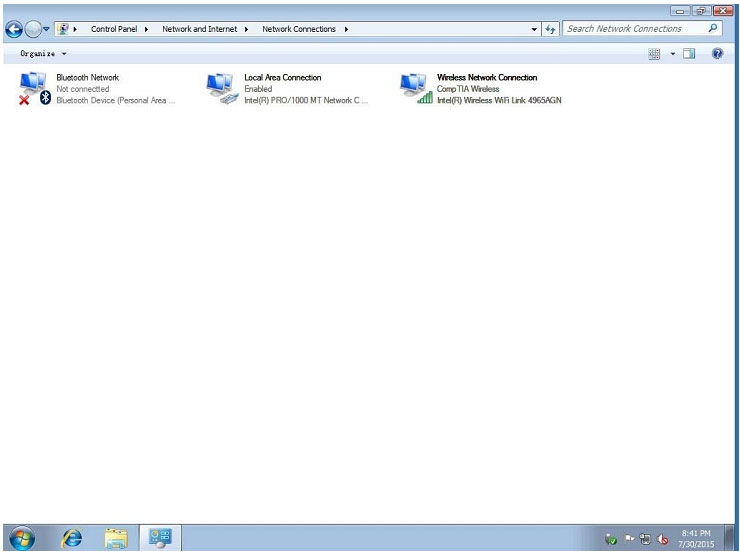
Correct Answer: Review the explanation for all details.
QUESTION 49
The network administrator has changed the IP address of ComputerA from 192.168.1.20 to 10.10.10.20 and now Jane, a user, is unable to connect to file shares on ComputerA from ComputerB using the computer name.
Instructions:
Using the available tools, resolve the connectivity issues. When you have completed the simulation, please select the done button
to submit your answer.
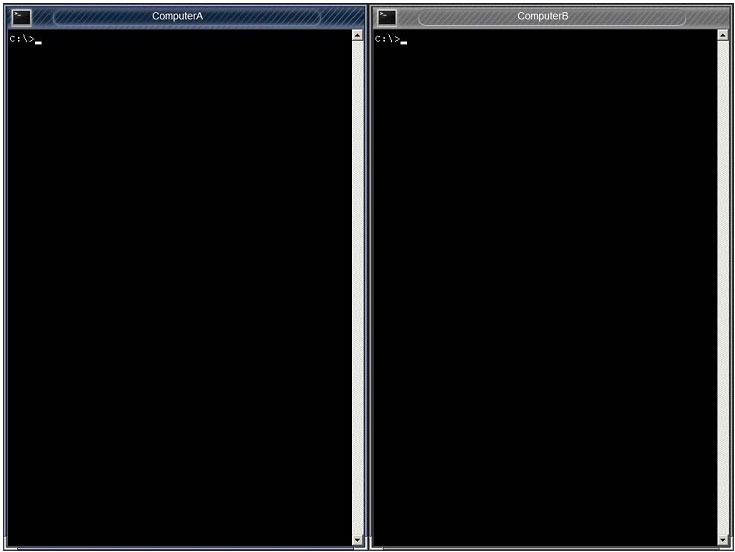
Correct Answer: Review the explanation for all details.
QUESTION 50
DRAG DROP
A technician has verified that Joe, a user, has a malware infection on his desktop. Drag and drop the following malware remediation techniques in the correct order Joe should follow to alleviate this issue.
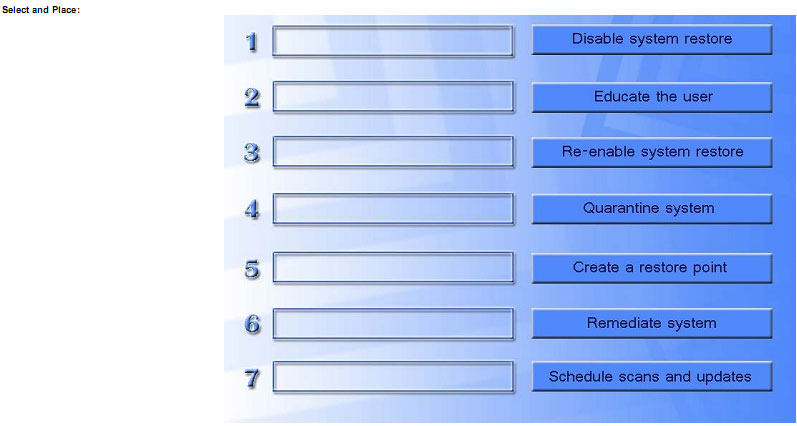
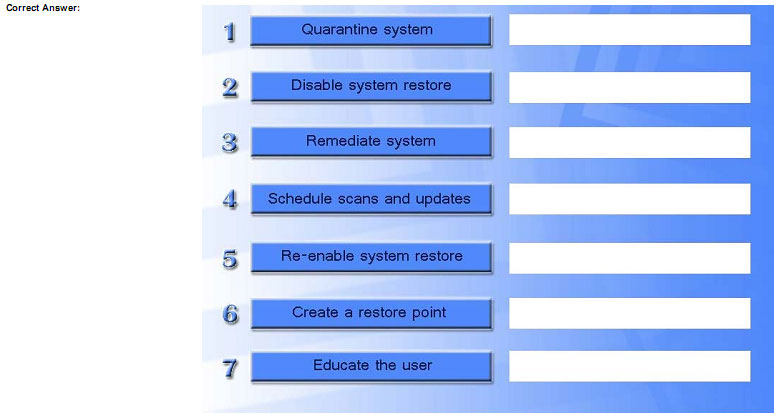
About the exam:
necessary skills for an entry-level IT professional. Successful candidates will have the knowledge required to:
• Assemble components based on customer requirements
• Install, configure and maintain devices, PCs and software for end users
• Understand the basics of networking and security/forensics
• Properly and safely diagnose, resolve and document common hardware and software issues
• Apply troubleshooting skills
• Provide appropriate customer support
• Understand the basics of virtualization, desktop imaging and deployment
Conclusion:
Certfans free share effective CompTIA A+ 220-902 exam dumps and 220-902 pdf download online,
free content can help you unravel a lot of doubts, want to obtain a certificate please choose the full 220-902 exam dumps.
Certfans all free content from Pass4itsure experts, we recommend that you choose him and want to obtain a certificate at
once please select https://www.pass4itsure.com/220-902.html PDF + VCE
[PDF] Free CompTIA A+ 220-902 dumps download from Google Drive:
https://drive.google.com/open?id=1I4jaW20oyakGy4HS1-ZpIJK_QmwUPEEZ
[PDF] Free Full CompTIA dumps download from Google Drive: https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
Pass4itsure Promo Code 15% Off
related: https://www.certfans.com/discount-cisco-iins-210-260-dumps-exam/