Certfans is a blog that shares free exam dumps, we update all year round, and we help all friends who need to
open the door to learning. Latest CompTIA security+ jk0-018 exam dumps from pass4itsure CompTIA experts,
free online jk0-018 exam exercises and jk0-018 PDF downloads, If you want to pass the JK0-018 exam
for the first time, please select the full and effective jk0-018 questions and answers.
https://www.pass4itsure.com/jk0-018.html provides PDF + VCE mode to help you easily get a certificate
[PDF] Free CompTIA Security+ JK0-018 dumps download from Google Drive:
https://drive.google.com/open?id=1ZvPlCzDTrntMmGkVVE0rI_ufYnwUtXIv
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
CompTIA Security+ Certification – CompTIA IT Certifications:https://certification.comptia.org/certifications/security
Pass4itsure offers the latest CompTIA Security+ JK0-018 practice test free of charge (100Q&As)
QUESTION 1
Which of the following application security testing techniques is implemented when an automated system generates random input data?
A. Fuzzing
B. XSRF
C. Hardening
D. Input validation
Correct Answer: A
QUESTION 2
Which of the following can be used by a security administrator to successfully recover a user’s forgotten password on a password protected file?
A. Cognitive password
B. Password sniffing
C. Brute force
D. Social engineering
Correct Answer: C
QUESTION 3
A security administrator wants to check user password complexity. Which of the following is the BEST tool to use?
A. Password history
B. Password logging
C. Password cracker
D. Password hashing
Correct Answer: C
QUESTION 4
Certificates are used for: (Select TWO).
A. Client authentication.
B. WEP encryption.
C. Access control lists.
D. Code signing.
E. Password hashing.
Correct Answer: AD
QUESTION 5
Which of the following is a hardware based encryption device?
A. EFS
B. TrueCrypt
C. TPM
D. SLE
Correct Answer: C
QUESTION 6
Which of the following BEST describes a protective countermeasure for SQL injection?
A. Eliminating cross-site scripting vulnerabilities
B. Installing an IDS to monitor network traffic
C. Validating user input in web applications
D. Placing a firewall between the Internet and database servers
Correct Answer: C
QUESTION 7
Which of the following MOST interferes with network-based detection techniques?
A. Mime-encoding
B. SSL
C. FTP
D. Anonymous email accounts
Correct Answer: B
QUESTION 8
A certificate authority takes which of the following actions in PKI?
A. Signs and verifies all infrastructure messages
B. Issues and signs all private keys
C. Publishes key escrow lists to CRLs
D. Issues and signs all root certificates
Correct Answer: D
QUESTION 9
Use of a smart card to authenticate remote servers remains MOST susceptible to which of the following attacks?
A. Malicious code on the local system
B. Shoulder surfing
C. Brute force certificate cracking
D. Distributed dictionary attacks
Correct Answer: A
QUESTION 10
Separation of duties is often implemented between developers and administrators in order to separate which of the following?
A. More experienced employees from less experienced employees
B. Changes to program code and the ability to deploy to production
C. Upper level management users from standard development employees
D. The network access layer from the application access layer
Correct Answer: B
QUESTION 11
A security administrator needs to update the OS on all the switches in the company. Which of the following MUST be done before any actual switch configuration is performed?
A. The request needs to be sent to the incident management team.
B. The request needs to be approved through the incident management process.
C. The request needs to be approved through the change management process.
D. The request needs to be sent to the change management team.
Correct Answer: C
QUESTION 12
Jane, an individual, has recently been calling various financial offices pretending to be another person to gain financial information. Which of the following attacks is being described?
A. Phishing
B. Tailgating
C. Pharming
D. Vishing
Correct Answer: D
QUESTION 13
A user in the company is in charge of various financial roles but needs to prepare for an upcoming audit. They use the same account to access each financial system. Which of the following security controls will MOST likely be implementedwithin the company?
A. Account lockout policy
B. Account password enforcement
C. Password complexity enabled
D. Separation of duties
Correct Answer: D
QUESTION 14
A CRL is comprised oF.
A. Malicious IP addresses.
B. Trusted CA’s.
C. Untrusted private keys.
D. Public keys.
Correct Answer: D
QUESTION 15
Sara, a user, downloads a keygen to install pirated software. After running the keygen, system performance is extremely slow and numerous antivirus alerts are displayed. Which of the following BEST describes this type of malware?
A. Logic bomb
B. Worm
C. Trojan
D. Adware
Correct Answer: C
QUESTION 16
Which of the following may significantly reduce data loss if multiple drives fail at the same time?
A. Virtualization
B. RAID
C. Load balancing
D. Server clustering
Correct Answer: B
QUESTION 17
Which of the following should be considered to mitigate data theft when using CAT5 wiring?
A. CCTV
B. Environmental monitoring
C. Multimode fiber
D. EMI shielding
Correct Answer: D
QUESTION 18
To help prevent unauthorized access to PCs, a security administrator implements screen savers that lock the PC after five minutes of inactivity. Which of the following controls is being described in this situation?
A. Management
B. Administrative
C. Technical
D. Operational
Correct Answer: C
QUESTION 19
Pete, a network administrator, is capturing packets on the network and notices that a large amount of the traffic on the LAN is SIP and RTP protocols. Which of the following should he do to segment that traffic from the other traffic?
A. Connect the WAP to a different switch.
B. Create a voice VLAN.
C. Create a DMZ.
D. Set the switch ports to 802.1q mode.
Correct Answer: B
QUESTION 20
Which of the following IP addresses would be hosts on the same subnet given the subnet mask 255.255.255.224? (Select TWO).
A. 10.4.4.125
B. 10.4.4.158
C. 10.4.4.165
D. 10.4.4.189
E. 10.4.4.199
Correct Answer: CD
QUESTION 21
Which of the following algorithms has well documented collisions? (Select TWO).
A. AES
B. MD5
C. SHA
D. SHA-256
E. RSA
Correct Answer: BC
QUESTION 22
Which of the following is BEST used as a secure replacement for TELNET?
A. HTTPS
B. HMAC
C. GPG
D. SSH
Correct Answer: D
QUESTION 23
An email client says a digital signature is invalid and the sender cannot be verified. The recipient is concerned with which of the following concepts?
A. Integrity
B. Availability
C. Confidentiality
D. Remediation
Correct Answer: A
QUESTION 24
Which of the following is an effective way to ensure the BEST temperature for all equipment within a datacenter?
A. Fire suppression
B. Raised floor implementation
C. EMI shielding
D. Hot or cool aisle containment
Correct Answer: D
QUESTION 25
Which of the following transportation encryption protocols should be used to ensure maximum security between a web browser and a web server?A. SSLv2
B. SSHv1
C. RSA
D. TLS
Correct Answer: D
QUESTION 26
Developers currently have access to update production servers without going through an approval process. Which of the following strategies would BEST mitigate this risk?
A. Incident management
B. Clean desk policy
C. Routine audits
D. Change management
Correct Answer: D
QUESTION 27
Which of the following is a difference between TFTP and FTP?
A. TFTP is slower than FTP.
B. TFTP is more secure than FTP.
C. TFTP utilizes TCP and FTP uses UDP.
D. TFTP utilizes UDP and FTP uses TCP.
Correct Answer: D
QUESTION 28
Matt, an administrator, notices a flood fragmented packet and retransmits from an email server. After disabling the TCP offload setting on the NIC, Matt sees normal traffic with packets flowing in sequence again.
Which of the following utilities was he MOST likely using to view this issue?
A. Spam filter
B. Protocol analyzer
C. Web application firewall
D. Load balancer
Correct Answer: B
QUESTION 29
Which of the following is characterized by an attacker attempting to map out an organization’s staff hierarchy in order to send targeted emails?
A. Whaling
B. Impersonation
C. Privilege escalation
D. Spear phishing
Correct Answer: A
QUESTION 30
Which of the following would a security administrator implement in order to discover comprehensive security threats on a network?
A. Design reviews
B. Baseline reporting
C. Vulnerability scan
D. Code review
Correct Answer: C
QUESTION 31
Which of the following is an example of a false positive?
A. Anti-virus identifies a benign application as malware.
B. A biometric iris scanner rejects an authorized user wearing a new contact lens.
C. A user account is locked out after the user mistypes the password too many times.
D. The IDS does not identify a buffer overflow.
Correct Answer: A
QUESTION 32
Data execution prevention is a feature in most operating systems intended to protect against which type of attack?
A. Cross-site scripting
B. Buffer overflow
C. Header manipulation
D. SQL injection
Correct Answer: B
QUESTION 33
Use of group accounts should be minimized to ensure which of the following?
A. Password security
B. Regular auditing
C. Baseline management
D. Individual accountability
Correct Answer: D
QUESTION 34
Privilege creep among long-term employees can be mitigated by which of the following procedures?
A. User permission reviews
B. Mandatory vacations
C. Separation of duties
D. Job function rotation
Correct Answer: A
QUESTION 35
In which of the following scenarios is PKI LEAST hardened?
A. The CRL is posted to a publicly accessible location.
B. The recorded time offsets are developed with symmetric keys.
C. A malicious CA certificate is loaded on all the clients.
D. All public keys are accessed by an unauthorized user.
Correct Answer: C
QUESTION 36
Configuring the mode, encryption methods, and security associations are part of which of the following?
A. IPSec
B. Full disk encryption
C. 802.1x
D. PKI
Correct Answer: A
QUESTION 37
Which of the following assessments would Pete, the security administrator, use to actively test that an application’s security controls are in place?
A. Code review
B. Penetration test
C. Protocol analyzerD. Vulnerability scan
Correct Answer: B
QUESTION 38
A security administrator has just finished creating a hot site for the company. This implementation relates to which of the following concepts?
A. Confidentiality
B. Availability
C. Succession planning
D. Integrity
Correct Answer: B
QUESTION 39
In the initial stages of an incident response, Matt, the security administrator, was provided the hard drives in question from the incident manager. Which of the following incident response procedures would he need to perform in order to begin
the analysis? (Select TWO).
A. Take hashes
B. Begin the chain of custody paperwork
C. Take screen shots
D. Capture the system image
E. Decompile suspicious files
Correct Answer: AD
QUESTION 40
Which of the following is used to certify intermediate authorities in a large PKI deployment?
A. Root CA
B. Recovery agent
C. Root user
D. Key escrow
Correct Answer: A
QUESTION 41
Which of the following components MUST be trusted by all parties in PKI?
A. Key escrow
B. CA
C. Private key
D. Recovery key
Correct Answer: B
QUESTION 42
Which of the following should Matt, a security administrator, include when encrypting smartphones? (Select TWO).
A. Steganography images
B. Internal memory
C. Master boot records
D. Removable memory cards
E. Public keys
Correct Answer: BD
QUESTION 43
Which of the following is the below pseudo-code an example of?
IF VARIABLE (CONTAINS NUMBERS = TRUE) THEN EXIT
A. Buffer overflow prevention
B. Input validation
C. CSRF prevention
D. Cross-site scripting prevention
Correct Answer: B
QUESTION 44
A system administrator is using a packet sniffer to troubleshoot remote authentication. The administrator detects a device trying to communicate to TCP port 49.
Which of the following authentication methods is MOST likely being attempted?
A. RADIUS
B. TACACS+
C. Kerberos
D. LDAP
Correct Answer: B
QUESTION 45
Which of the following can use RC4 for encryption? (Select TWO).
A. CHAP
B. SSL
C. WEP
D. AES
E. 3DES
Correct Answer: BC
QUESTION 46
Which of the following defines a business goal for system restoration and acceptable data loss?
A. MTTR
B. MTBF
C. RPO
D. Warm site
Correct Answer: C
QUESTION 47
If Organization A trusts Organization B and Organization B trusts Organization C, then Organization A trusts Organization C.
Which of the following PKI concepts is this describing?
A. Transitive trust
B. Public key trust
C. Certificate authority trust
D. Domain level trust
Correct Answer: A
QUESTION 48
Which of the following concepts is BEST described as developing a new chain of command in the event of a contingency?
A. Business continuity planning
B. Continuity of operations
C. Business impact analysis
D. Succession planning
Correct Answer: D
QUESTION 49
Which of the following allows a company to maintain access to encrypted resources when employee turnover is high?A. Recovery agent
B. Certificate authority
C. Trust model
D. Key escrow
Correct Answer: A
QUESTION 50
Which of the following devices will help prevent a laptop from being removed from a certain location?
A. Device encryption
B. Cable locks
C. GPS tracking
D. Remote data wipes
Correct Answer: B
QUESTION 51
Which of the following protocols would be implemented to secure file transfers using SSL?
A. TFTP
B. SCP
C. SFTP
D. FTPS
Correct Answer: D
QUESTION 52
Which of the following are used to implement VPNs? (Select TWO).
A. SFTP
B. IPSec
C. HTTPS
D. SNMP
E. SSL
Correct Answer: BE
QUESTION 53
A company recently implemented a TLS on their network. The company is MOST concerned with:
A. Confidentiality
B. Availability
C. Integrity
D. Accessibility
Correct Answer: A
QUESTION 54
Which of the following describes how an attacker can send unwanted advertisements to a mobile device?
A. Man-in-the-middle
B. Bluejacking
C. Bluesnarfing
D. Packet sniffing
Correct Answer: B
QUESTION 55
A network device that protects an enterprise based only on source and destination addresses is BEST described as:
A. IDS.
B. ACL.
C. Stateful packet filtering.
D. Simple packet filtering.
Correct Answer: D
QUESTION 56
A human resources employee receives an email from a family member stating there is a new virus going around. In order to remove the virus, a user must delete the Boot.ini file from the system immediately. This is an example of which of the
following?
A. Hoax
B. Spam
C. Whaling
D. Phishing
Correct Answer: A
QUESTION 57
A third party application has the ability to maintain its own user accounts or it may use single sign-on. To use single sign-on, the application is requesting the following information: OU=Users, DC=Domain, DC=COM. This application is
requesting which of the following authentication services?
A. TACACS+
B. RADIUS
C. LDAP
D. Kerberos
Correct Answer: C
QUESTION 58
Power and data cables from the network center travel through the building’s boiler room. Which of the following should be used to prevent data emanation?
A. Video monitoring
B. EMI shielding
C. Plenum CAT6 UTP
D. Fire suppression
Correct Answer: B
QUESTION 59
Which of the following must a security administrator implement to isolate public facing servers from both the corporate network and the Internet?
A. NAC
B. IPSec
C. DMZ
D. NAT
Correct Answer: C
QUESTION 60
Which of the following protocols provides fast, unreliable file transfer?
A. TFTP
B. SFTP
C. Telnet
D. FTPS
Correct Answer: A
QUESTION 61
Which of the following digital certificate management practices will ensure that a lost certificate is not compromised?
A. Key escrowB. Non-repudiation
C. Recovery agent
D. CRL
Correct Answer: D
QUESTION 62
A security administrator forgets their card to access the server room. The administrator asks a co-worker if they could use their card for the day. Which of the following is the administrator using to gain access to the server room?
A. Man-in-the-middle
B. Tailgating
C. Impersonation
D. Spoofing
Correct Answer: C
QUESTION 63
A security administrator has implemented a policy to prevent data loss. Which of the following is the BEST method of enforcement?
A. Internet networks can be accessed via personally-owned computers.
B. Data can only be stored on local workstations.
C. Wi-Fi networks should use WEP encryption by default.
D. Only USB devices supporting encryption are to be used.
Correct Answer: D
QUESTION 64
Symmetric encryption utilizes __________, while asymmetric encryption utilizes _________.
A. Public keys, one time
B. Shared keys, private keys
C. Private keys, session keys
D. Private keys, public keys
Correct Answer: B
QUESTION 65
The main corporate website has a service level agreement that requires availability 100% of the time, even in the case of a disaster. Which of the following would be required to meet this demand?
A. Warm site implementation for the datacenter
B. Geographically disparate site redundant datacenter
C. Localized clustering of the datacenter
D. Cold site implementation for the datacenter
Correct Answer: B
QUESTION 66
Which of the following is a vulnerability associated with disabling pop-up blockers?
A. An alert message from the administrator may not be visible
B. A form submitted by the user may not open
C. The help window may not be displayed
D. Another browser instance may execute malicious code
Correct Answer: D
QUESTION 67
A security technician needs to open ports on a firewall to allow for domain name resolution. Which of the following ports should be opened? (Select TWO).
A. TCP 21
B. TCP 23
C. TCP 53
D. UDP 23
E. UDP 53
Correct Answer: CE
QUESTION 68
During an anonymous penetration test, Jane, a system administrator, was able to identify a shared print spool directory, and was able to download a document from the spool. Which statement BEST describes her privileges?
A. All users have write access to the directory.
B. Jane has read access to the file.
C. All users have read access to the file.
D. Jane has read access to the directory.
Correct Answer: C
QUESTION 69
An IT security technician is actively involved in identifying coding issues for her company. Which of the following is an application security technique that can be used to identify unknown weaknesses within the code?
A. Vulnerability scanning
B. Denial of service
C. Fuzzing
D. Port scanning
Correct Answer: C
QUESTION 70
Which of the following data security techniques will allow Matt, an IT security technician, to encrypt a system with speed as its primary consideration?
A. Hard drive encryption
B. Infrastructure as a service
C. Software based encryption
D. Data loss prevention
Correct Answer: A
QUESTION 71
Matt, a forensic analyst, wants to obtain the digital fingerprint for a given message. The message is 160-bits long. Which of the following hashing methods would Matt have to use to obtain this digital fingerprint?
A. SHA1
B. MD2
C. MD4
D. MD5
Correct Answer: A
QUESTION 72
A system administrator is notified by a staff member that their laptop has been lost. The laptop contains the user’s digital certificate. Which of the following will help resolve the issue? (Select TWO).
A. Revoke the digital certificate
B. Mark the key as private and import it
C. Restore the certificate using a CRL
D. Issue a new digital certificate
E. Restore the certificate using a recovery agent
Correct Answer: AD
QUESTION 73
A security engineer is given new application extensions each month that need to be secured prior to implementation. They do not want the new extensions to invalidate or interfere with existing application security. Additionally, the engineer
wants to ensure that the new requirements are approved by the appropriate personnel. Which of the following should be in place to meet these two goals? (Select TWO).
A. Patch Audit Policy
B. Change Control PolicyC. Incident Management Policy
D. Regression Testing Policy
E. Escalation Policy
F. Application Audit Policy
Correct Answer: BD
QUESTION 74
During an audit, the security administrator discovers that there are several users that are no longer employed with the company but still have active user accounts. Which of the following should be performed?
A. Account recovery
B. Account disablement
C. Account lockouts
D. Account expiration
Correct Answer: B
QUESTION 75
A system administrator has concerns regarding their users accessing systems and secured areas using others’ credentials. Which of the following can BEST address this concern?
A. Create conduct policies prohibiting sharing credentials.
B. Enforce a policy shortening the credential expiration timeframe.
C. Implement biometric readers on laptops and restricted areas.
D. Install security cameras in areas containing sensitive systems.
Correct Answer: C
QUESTION 76
A network administrator has a separate user account with rights to the domain administrator group. However, they cannot remember the password to this account and are not able to login to the server when needed. Which of the following is
MOST accurate in describing the type of issue the administrator is experiencing?
A. Single sign-on
B. Authorization
C. Access control
D. Authentication
Correct Answer: D
QUESTION 77
Jane has implemented an array of four servers to accomplish one specific task. This is BEST known as which of the following?
A. Clustering
B. RAID
C. Load balancing
D. Virtualization
Correct Answer: A
QUESTION 78
Which of the following security account management techniques should a security analyst implement to prevent staff, who has switched company roles, from exceeding privileges?
A. Internal account audits
B. Account disablement
C. Time of day restriction
D. Password complexity
Correct Answer: A
QUESTION 79
To ensure compatibility with their flagship product, the security engineer is tasked to recommend an encryption cipher that will be compatible with the majority of third party software and hardware vendors. Which of the following should be
recommended?
A. SHA
B. MD5
C. Blowfish
D. AES
Correct Answer: D
QUESTION 80
After a new firewall has been installed, devices cannot obtain a new IP address. Which of the following ports should Matt, the security administrator, open on the firewall?
A. 25
B. 68
C. 80
D. 443
Correct Answer: B
QUESTION 81
A system administrator has noticed that users change their password many times to cycle back to the original password when their passwords expire. Which of the following would BEST prevent this behavior?
A. Assign users passwords based upon job role.
B. Enforce a minimum password age policy.
C. Prevent users from choosing their own passwords.
D. Increase the password expiration time frame.
Correct Answer: B
QUESTION 82
The systems administrator notices that many employees are using passwords that can be easily guessed or are susceptible to brute force attacks. Which of the following would BEST mitigate this risk?
A. Enforce password rules requiring complexity.
B. Shorten the maximum life of account passwords.
C. Increase the minimum password length.
D. Enforce account lockout policies.
Correct Answer: A
QUESTION 83
Pete, a security analyst, has been tasked with explaining the different types of malware to his colleagues. The two malware types that the group seems to be most interested in are botnets and viruses. Which of the following explains the
difference between these two types of malware?
A. Viruses are a subset of botnets which are used as part of SYN attacks.
B. Botnets are a subset of malware which are used as part of DDoS attacks.
C. Viruses are a class of malware which create hidden openings within an OS.
D. Botnets are used within DR to ensure network uptime and viruses are not.
Correct Answer: B
QUESTION 84
A security analyst implemented group-based privileges within the company active directory. Which of the following account management techniques should be undertaken regularly to ensure least privilege principles?
A. Leverage role-based access controls.
B. Perform user group clean-up.
C. Verify smart card access controls.
D. Verify SHA-256 for password hashes.
Correct Answer: B
QUESTION 85
A technician has just installed a new firewall onto the network. Users are reporting that they cannot reach any website. Upon further investigation, the technician determines that websites can be reached by entering their IP addresses. Which
of the following ports may have been closed to cause this issue?
A. HTTPB. DHCP
C. DNS
D. NetBIOS
Correct Answer: C
QUESTION 86
The system administrator has been notified that many users are having difficulty connecting to the company’s wireless network. They take a new laptop and physically go to the access point and connect with no problems. Which of the
following would be the MOST likely cause?
A. The certificate used to authenticate users has been compromised and revoked.
B. Multiple war drivers in the parking lot have exhausted all available IPs from the pool to deny access.
C. An attacker has gained access to the access point and has changed the encryption keys.
D. An unauthorized access point has been configured to operate on the same channel.
Correct Answer: D
QUESTION 87
The systems administrator wishes to implement a hardware-based encryption method that could also be used to sign code. They can achieve this by:
A. Utilizing the already present TPM.
B. Configuring secure application sandboxes.
C. Enforcing whole disk encryption.
D. Moving data and applications into the cloud.
Correct Answer: A
QUESTION 88
The Chief Information Security Officer (CISO) has mandated that all IT systems with credit card data be segregated from the main corporate network to prevent unauthorized access and that access to the IT systems should be logged. Which
of the following would BEST meet the CISO’s requirements?
A. Sniffers
B. NIDS
C. Firewalls
D. Web proxies
E. Layer 2 switches
Correct Answer: C
QUESTION 89
One of the servers on the network stops responding due to lack of available memory. Server administrators did not have a clear definition of what action should have taken place based on the available memory. Which of the following would
have BEST kept this incident from occurring?
A. Set up a protocol analyzer
B. Set up a performance baseline
C. Review the systems monitor on a monthly basis
D. Review the performance monitor on a monthly basis
Correct Answer: B
QUESTION 90
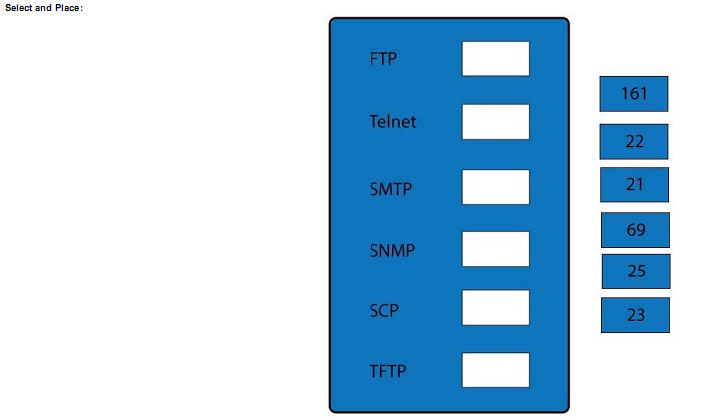
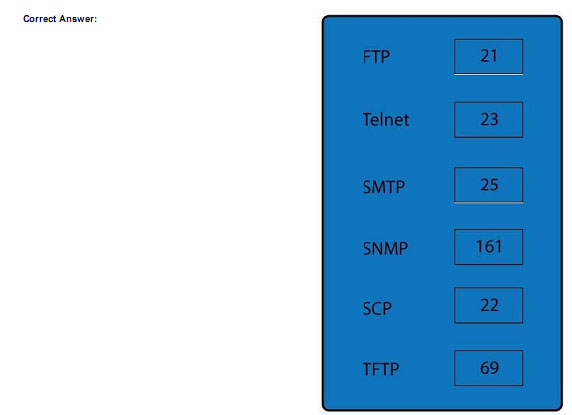
DRAG DROP
Drag and drop the correct protocol to its default port.
QUESTION 91
DRAG DROP
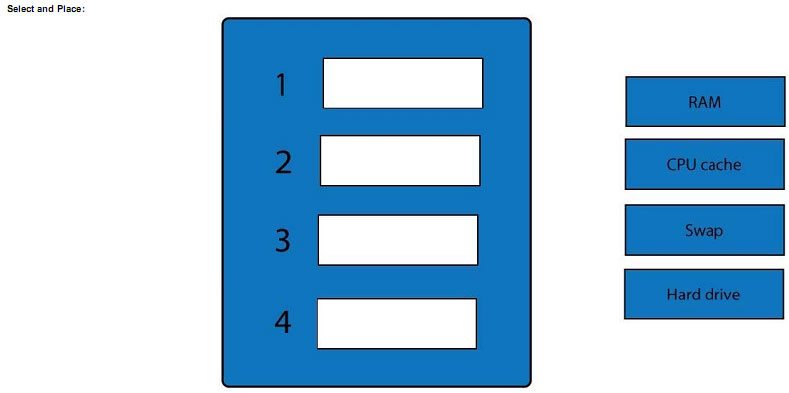
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them
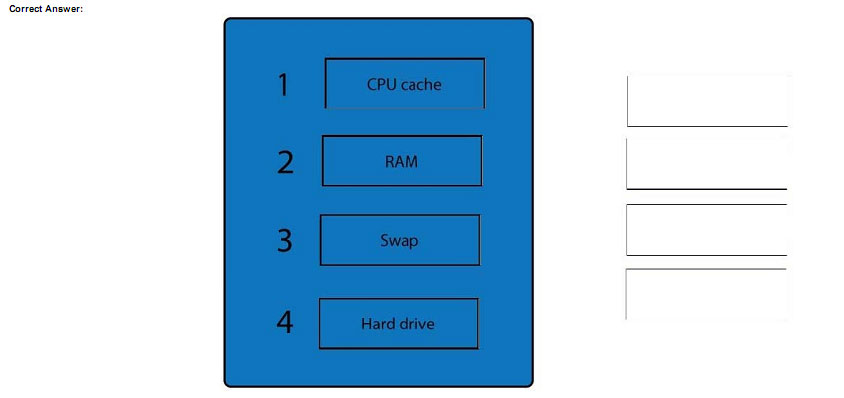
QUESTION 92
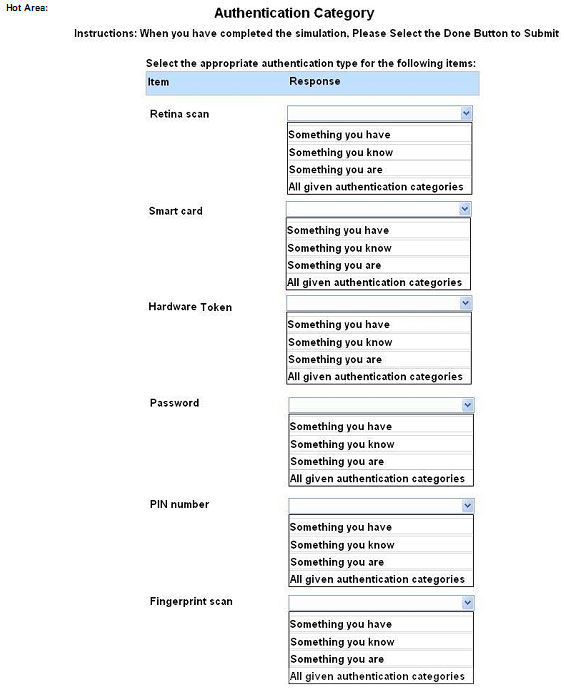
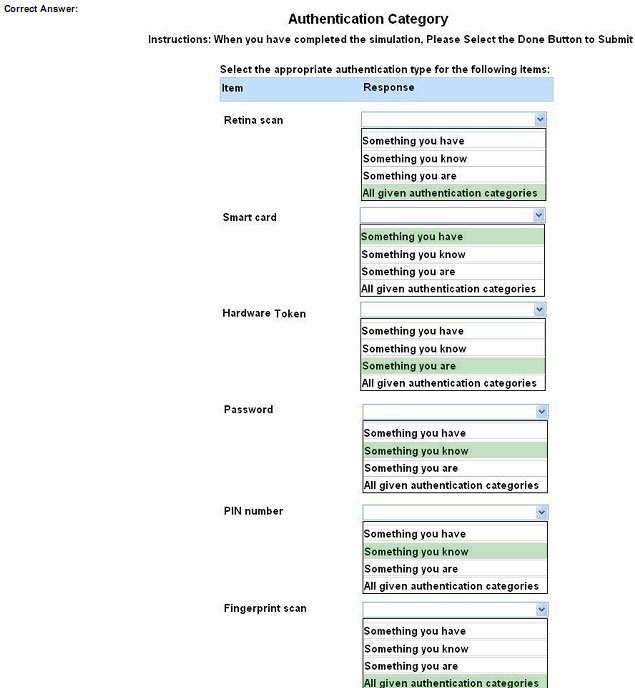
HOTSPOT
For each of the given items, select the appropriate authentication category from the dropdown choices.
Instructions: When you have completed the simulation, please select the Done button to submit
QUESTION 93
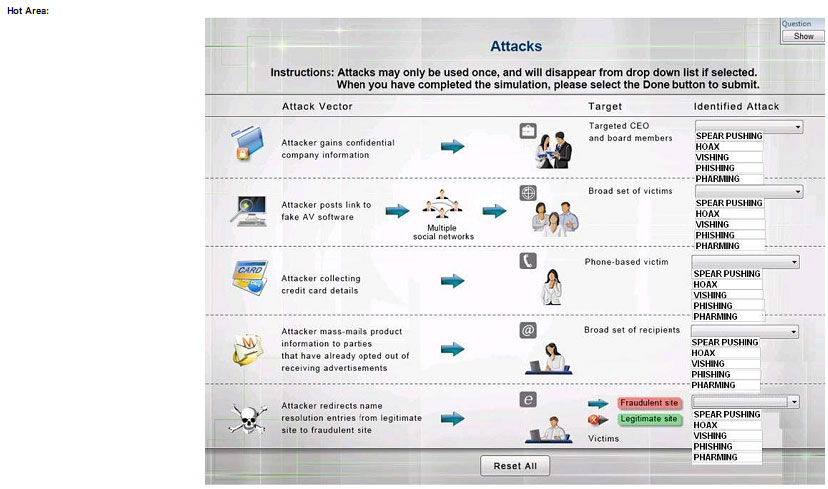
HOTSPOT
Select the appropriate attack from each drop down list to label the corresponding illustrated attack.
Instructions: Attacks may only be used once, and will disappear from drop down list if selected. When you have completed the simulation, please select the Done button to submit.
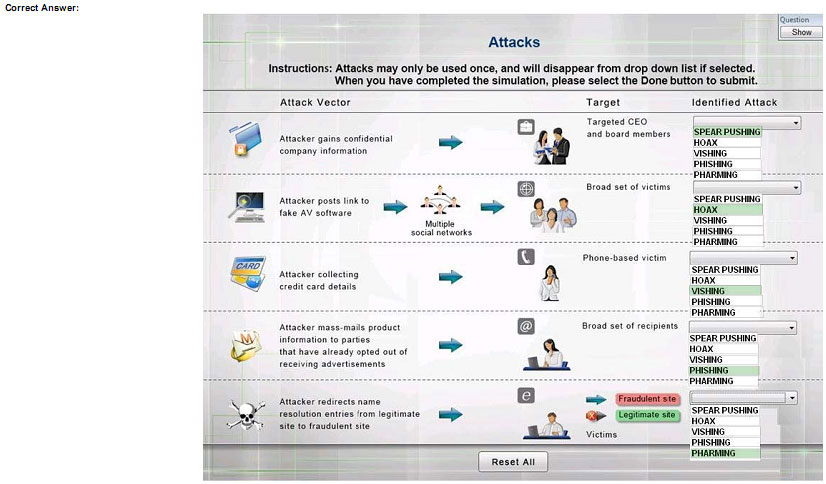
QUESTION 94
HOTSPOT
For each of the given items, select the appropriate authentication category from the drop down choices.
Select the appropriate authentication type for the following items:
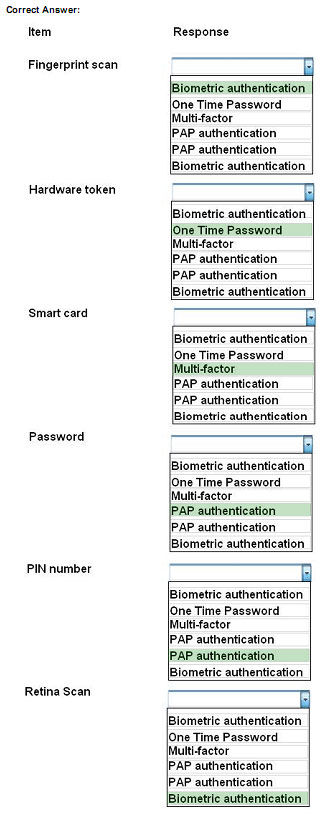
QUESTION 95
DRAG DROP
A Security administrator wants to implement strong security on the company smart phones and terminal servers located in the data center. Drag and Drop the applicable controls to each asset type.
Instructions: Controls can be used multiple times and not all placeholders needs to be filled. When you have completed the simulation, Please select Done to submit.
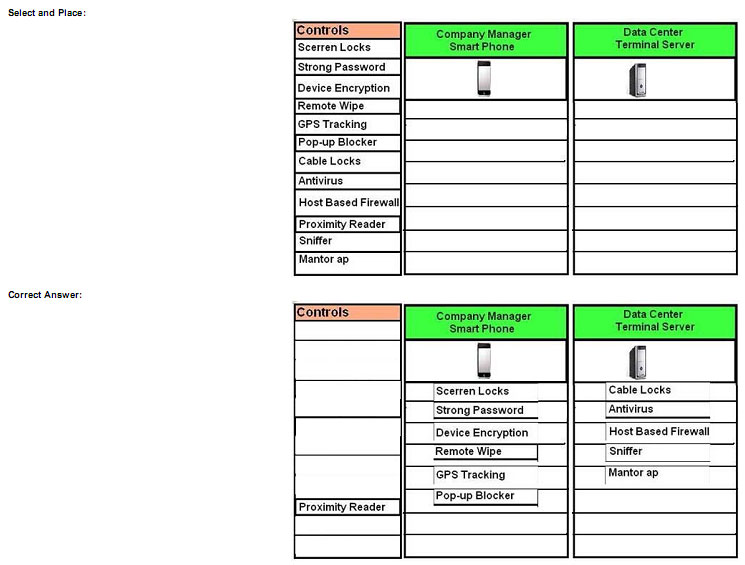
QUESTION 96
DRAG DROPDetermine the types of Attacks from right to specific action
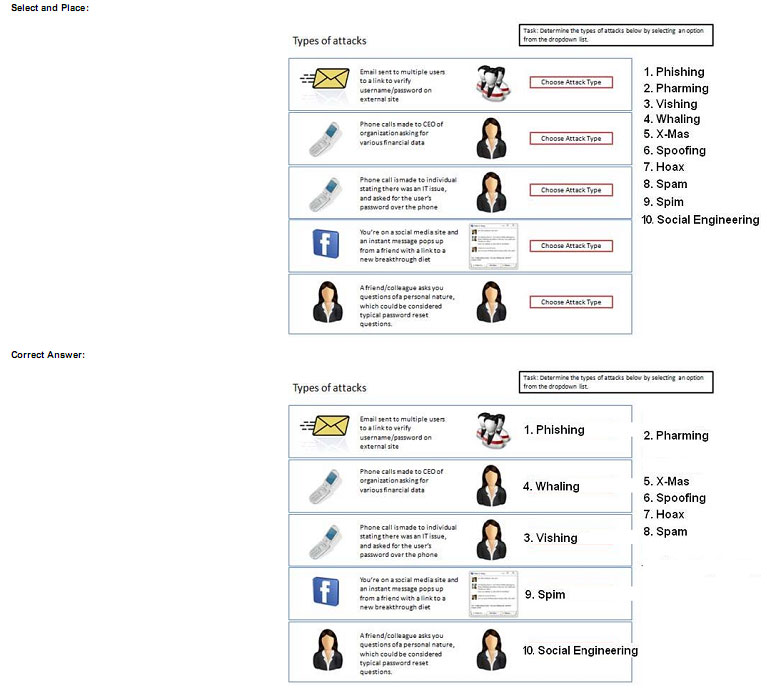
QUESTION 97
DRAG DROP
You are the security administrator. You need to determine the types of security. Drag the items “Types of Security” to appropriate Security devices.
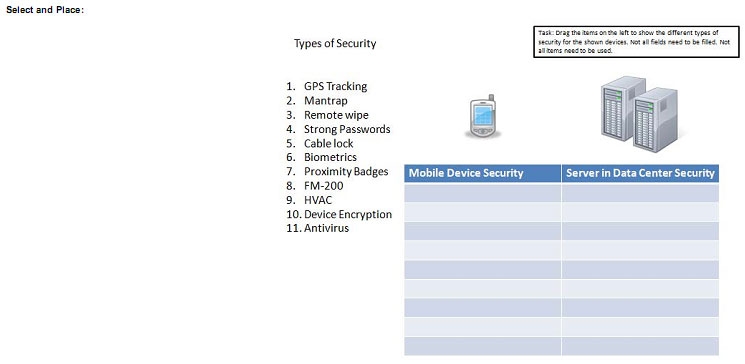
QUESTION 98
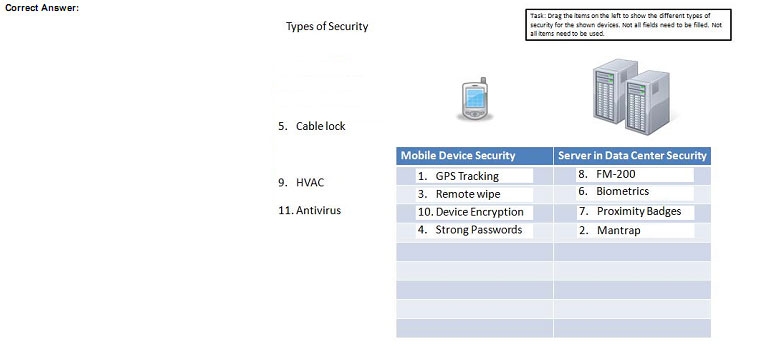
You are the security administrator. You need to determine the types of security. Drag the items “Types of Security” to appropriate Security devices.
Correct Answer: Use the following answer for this simulation task.
QUESTION 99
DRAG DROP
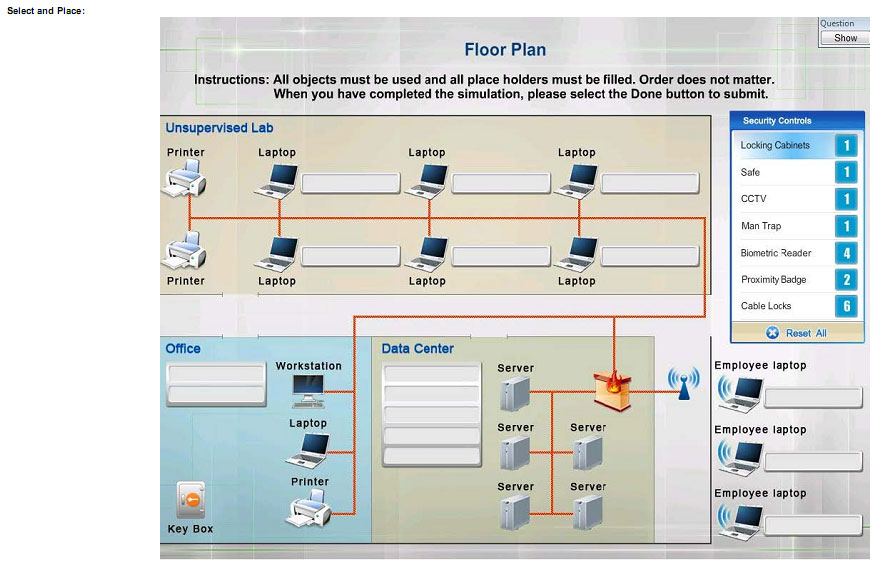
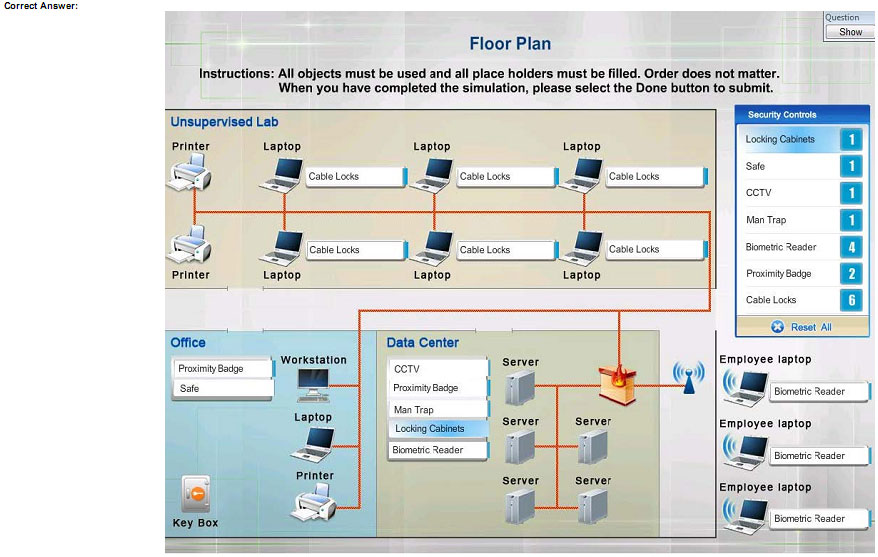
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan-Instructions: All objects must be used and all place holders must be filled Order does not matter When
you have completed the simulation, please select the Done button to submit
QUESTION 100
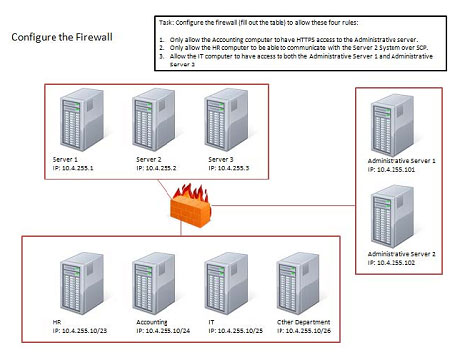
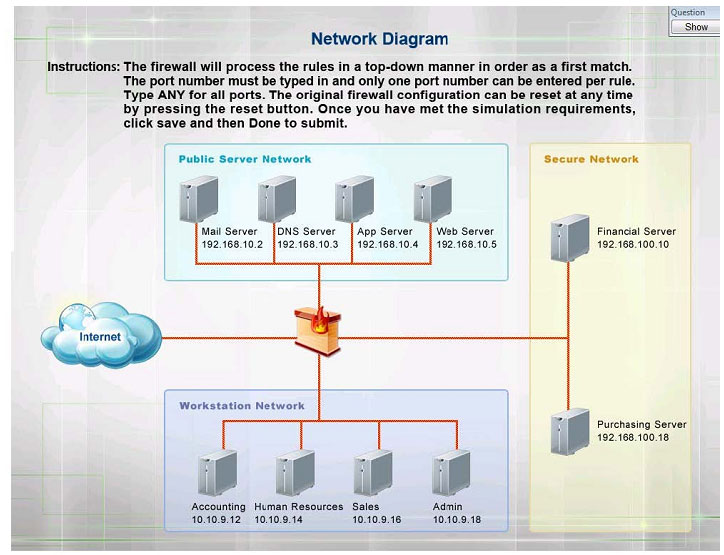
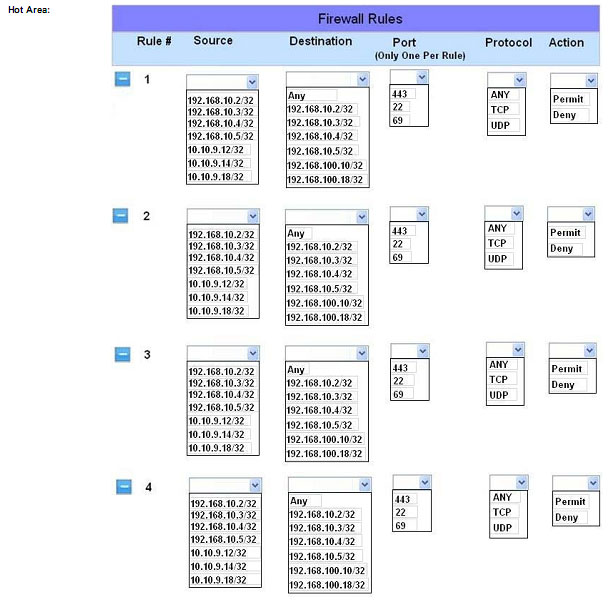
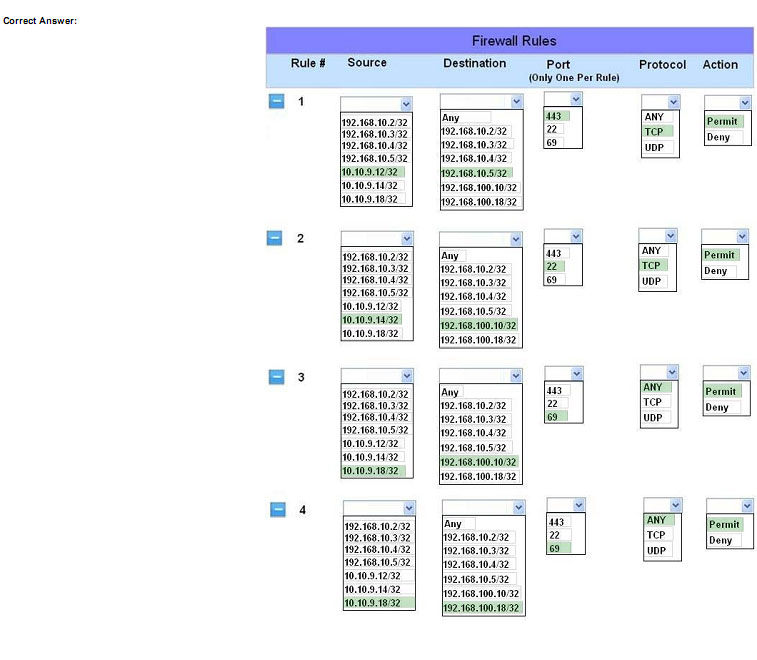
HOTSPOT
The security administrator has installed a new firewall which implements an implicit DENY policy by default Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port.
3. The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port number must be typed in and only one port number can be entered per rule Type ANY for all ports. The original firewall configuration can
be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submi
About the exam:
CompTIA Security+ is the first security certification IT professionals should earn. It establishes the core knowledge required of
any cybersecurity role and provides a springboard to intermediate-level cybersecurity jobs. Security+ incorporates best
practices in hands-on trouble-shooting to ensure security professionals have practical security problem-solving skills.
Cybersecurity professionals with Security+ know how to address security incidents – not just identify them.
Conclusion:
Certfans free share effective CompTIA security+ jk0-018 exam dumps and jk0-018 pdf download online,
free content can help you unravel a lot of doubts, want to obtain a certificate please choose the full jk0-018 exam dumps.
Certfans all free content from Pass4itsure experts, we recommend that you choose him and want to obtain a certificate at
once please select https://www.pass4itsure.com/jk0-018.html PDF + VCE
[PDF] Free CompTIA Security+ JK0-018 dumps download from Google Drive:
https://drive.google.com/open?id=1ZvPlCzDTrntMmGkVVE0rI_ufYnwUtXIv
[PDF] Free Full CompTIA dumps download from Google Drive:
https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
Pass4itsure Promo Code 15% Off
related: https://www.certfans.com/most-popular-ccnp-routing-and-switching-300-135-dumps/